Controls that Ensure Accuracy of Asset Inventory

The Securities and Exchange Commission (SEC) defines controls as “…a specific set of policies, procedures, and activities designed to meet an objective. A control may exist within a designated function or activity in a process. Controls have unique characteristics – for example, they can be automated or manual; reconciliations; segregation of duties; review and approval authorizations; safeguarding and accountability of assets; preventing or detecting error or fraud…”
For IT Asset Management (ITAM) practice, the importance of an accurate and trustworthy inventory of IT assets is paramount. In another word, ensuring accurate inventory is one of the key objectives of ITAM practice. However, time and again ITAM practice fails to achieve that key objective. The reasons can vary, as well as the severity of its impact. Defining and implementing effective controls can alleviate churn and ensure that ITAM provides reliable asset inventory at all time.
This article aims to provide a simple, practical and effective approach to define and implement internal controls that ensure accuracy of IT asset inventory. This method can be applied to any asset type, hardware or software, for any platform, on-premise assets or Cloud assets, and controls can be automated for continual compliance.
Let’s start with the basics, Figure 1 shows five key activities (listed below) of IT asset lifecycle management process, sometimes they are called lifecycle “stages” and sometimes they are broken into more granular activities. In either case, this approach to define and implement controls will deliver the same result. One word of caution – apply controls at the right level to avoid complexity and unnecessary churn.
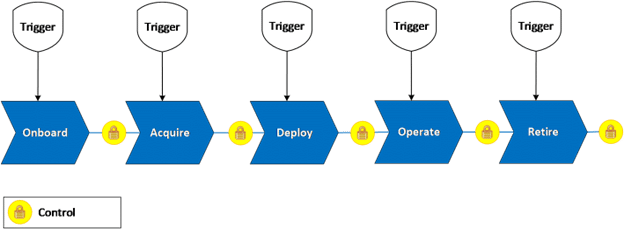
1. Onboard – This activity is to onboard a new asset that is not in the authorized list of assets. Onboarding of a new asset, hardware or software, should be done in a systemic way to ensure its compatibility, reliability and security with existing technology and business requirements.
2. Acquire – This activity is to fulfill user or consumer request for an asset (from the authorized list of assets) in a timely manner.
3. Deploy – This activity is to build and deploy the asset.
4. Operate – This activity is to manage Move, Add, Change, Delete (MACD) requests and related tasks during the “active” life of the asset.
5. Retire – This activity is to safely retire or dispose the asset.
More details about these activities can be found in IAITAM best practice books and ISO 19770-1.
A control is defined and implemented after each key activity so that the preceding activity provides required asset data or updates the data before next activity can be initiated. These activities do not occur in vacuum, each one of them is initiated by one or more IT processes. Some examples are:
– Onboarding of a new asset is triggered by Demand Management, Request Fulfillment or Project Management process
– Acquisition of an asset is triggered by Request Fulfillment or Project Management process
– Deployment of an asset is triggered by Change Management or Request Fulfillment process, so and so forth.
For a control to work effectively, ITAM needs to do some homework:
1. Clearly identify asset attributes that each activity must provide (or update). For example, after completion of the Acquire activity, asset must be registered in its Book of Record (BOR) with at least its physical identity attributes, such as serial number, make, model, etc. Similarly, after completion of the Deploy activity, asset status, its logical identity and location must be updated.
2. Define what each control will do if required asset data is not available in the asset BOR. The most effective “action” is to stop the triggering process and not allow it to complete. For example, if Change Management process triggers the Deploy activity, do not allow the change record to complete until required asset data has been updated in the asset BOR.
3. Work with relevant triggering process owners and ensure that these controls are implemented in those processes, most of them can be automated, but some may need manual intervention to comply with the control requirements.
4. Finally, a dashboard is necessary to show how many controls have failed and how many have succeeded. It should also show which triggering processes have not met the control requirements and processes that have met them. This gives full visibility of areas that require improvement and continually improve and maintain accuracy of asset inventory.
In summary, these are “activity” controls – controls that require triggering processes to include an activity to update asset BOR before they can complete, and these are detective controls – controls that detect occurrence of an activity that impacts asset data and error in the data. These controls help in maintaining accuracy of asset inventory (one of the ITAM objectives). Similar controls can be defined and implemented to address financial, reputational, legal and security risks related to IT assets. In addition, with proper technical capability, these controls can be continuously monitored, and issues fixed immediately to avoid last moment surprises.
 +1-330-628-3012
+1-330-628-3012 info@iaitam.org
info@iaitam.org