-

5 Ways AI and Automation Eliminate Compliance Risks in IT Asset Management
AI and automation reduce IT compliance risks, cut costs, and keep you audit-ready—so you stay in control of every software asset.
-

Bridging the Digital Divide: The Role of ITAD in Promoting Digital Inclusion
ITAD helps bridge the digital divide by repurposing retired tech, ensuring access to education, jobs, and essential services for those in need.
-

Globalizing ITAD: Ensuring Consistent Standards and Compliance Across Borders
As businesses expand globally, ITAD must ensure compliance, security, and sustainability while preventing e-waste dumping and data breaches.
-
Assessing Your ITAM Program Maturity
Determine what areas of your ITAM program are basic, reactive, proactive, service or value-add through a comprehensive program maturity assessment.
-

Understanding Entra Automated Provisioning and Its Benefits
Entra Automated Provisioning streamlines user account management, enhancing security, efficiency, and license visibility through automation and seamle
-
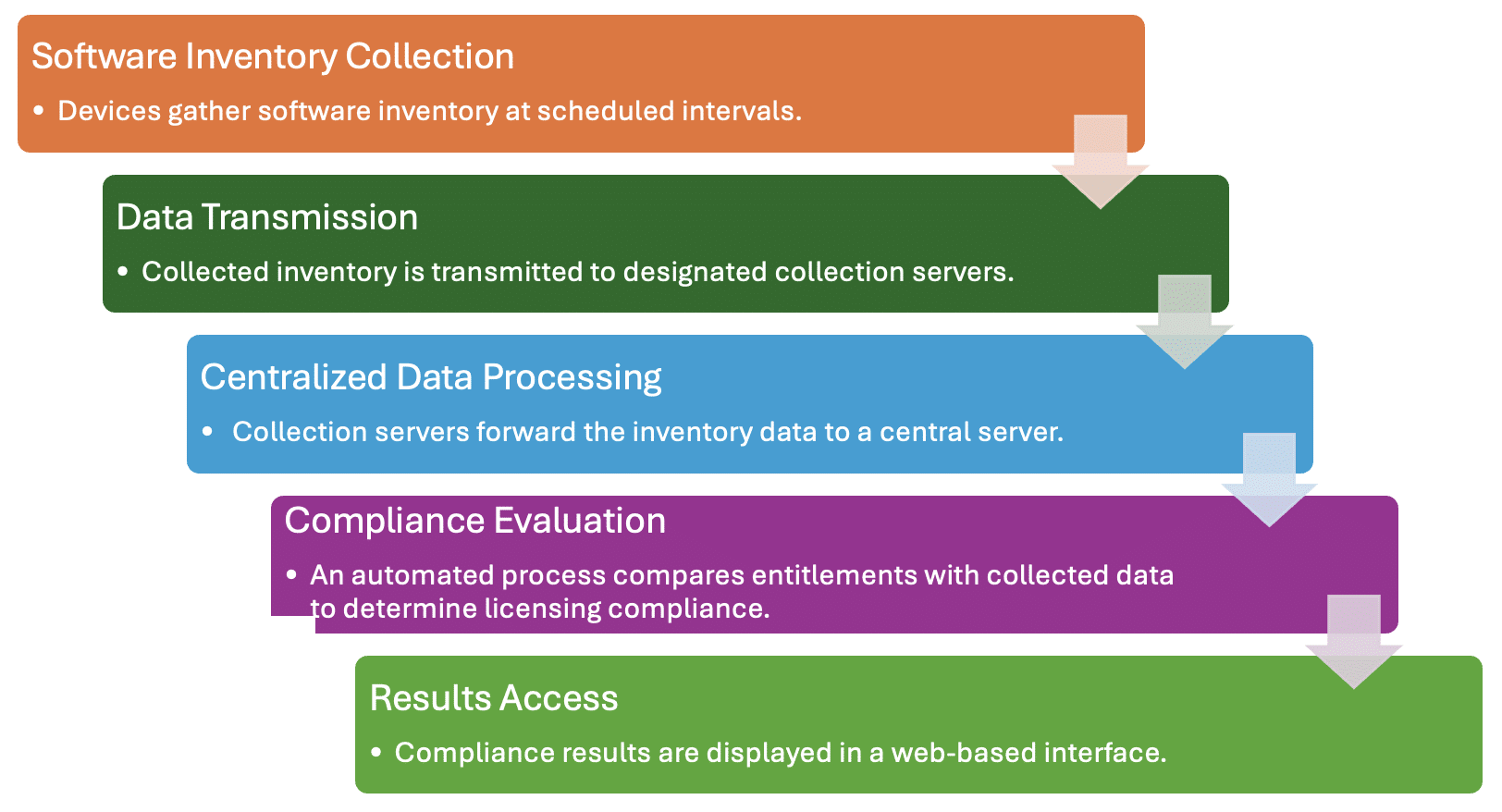
Making SAM Tools Work: Insights from the Trenches
Effective SAM tools require collaboration between IT support and SAM analysts to ensure reliable results and optimize licensing positions.
-

Integrating ITAM and ITAD for Enhanced Security and Corporate Sustainability
Merging ITAM and ITAD creates a unified approach that enhances data security while advancing sustainability goals for forward-thinking organizations.
-

Sims Lifecycle Services
IAITAM Provider Member Sims Lifecycle Services (SLS) is a global leader in IT asset disposition (ITAD) for enterprise companies, cloud providers and electronic manufacturers. With SLS, you’re not just getting an ITAD service; you’re partnering with a team committed to delivering compliant, data secure, end-to-end solutions worldwide. Our services cover a broad range of needs—from IT asset reuse, redeployment, recycling, on-site data destruction and data center decommissioning. In business since 2002, SLS continues to drive innovation and value recovery in both our industry and the circular economy, and ensures data safe solutions in everything we do. SLS is a key part of […]
-
Security, Compliance & Sustainability
Join us for our final Wednesday Webinar before we return on May 14th! In this insightful session, Jeff Datkuliak from ARCOA will explore the critical intersection of security, compliance, and sustainability in IT asset management. As organizations face increasing regulatory demands and rising environmental concerns, it’s essential to implement strategies that protect data, meet compliance…
-
Global ITAD Strategies: Sustainability, Market Trends & Scaling for Success
Join Craig Boswell, President of HOBI International, Inc., for an exclusive preview of the upcoming full session on global ITAD challenges. Craig will explore changes in ITAD sustainability, evolving client expectations, and strategies for scaling ITAD operations internationally. Gain insights into ESG compliance, global resale trends, and how to navigate ITAD across multiple regions. Don’t…





