-

Panning for Gold: Software Renewals Matter
In just making sure that renewals go downstream and get processed on time, your ITAM program is missing some SAM opportunities.
-

Navigating Risk Management in IT Asset Disposition (ITAD)
The complexity of IT Asset Disposition (ITAD) extends beyond merely disposing of outdated or unused IT equipment.
-
Improving Support to Increase ROI
Now that many organizations have shifted to hybrid or work-from-home models, their approach to IT asset management needs to shift as well.
-

Erase Data Remotely for Safeguarding Your Organization from Data Breach Risks
Remote data erasure enables organizations to securely erase data from endpoint devices used by the remote workforce to mitigate data breach risks.
-

ITAM and Green IT
Sustainable ITAM is an approach to IT management that considers environmental, social, and governance impacts.
-
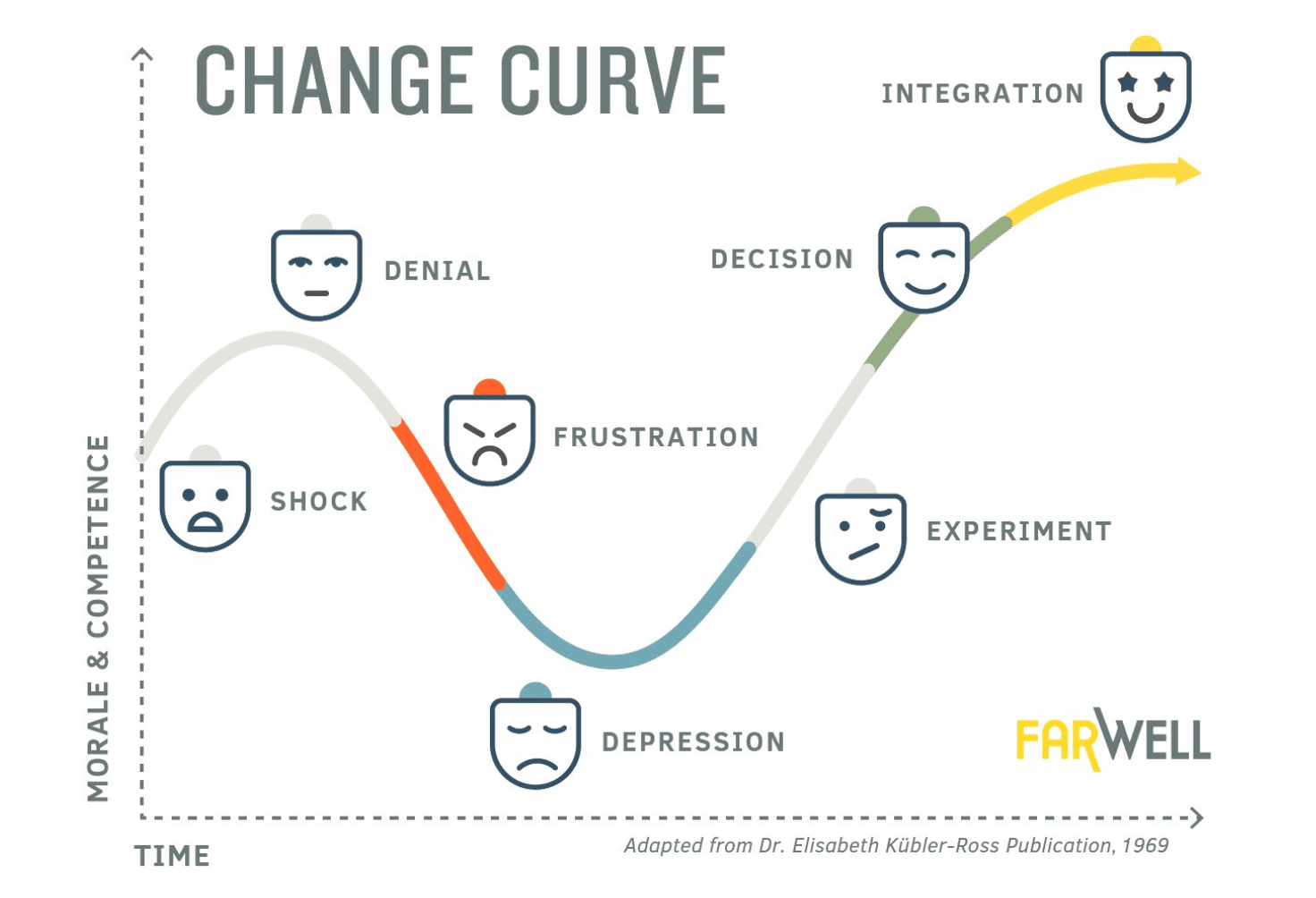
From Shock to Integration: A Journey Through the 7 Emotional Landscapes
When we embrace the Kübler-Ross change model, we don’t just make peace with change; we learn to lead the dance.
-

The Language of SAM
Making sure you are using the same communication terminology across departments is a key element for a successful SAM Program
-
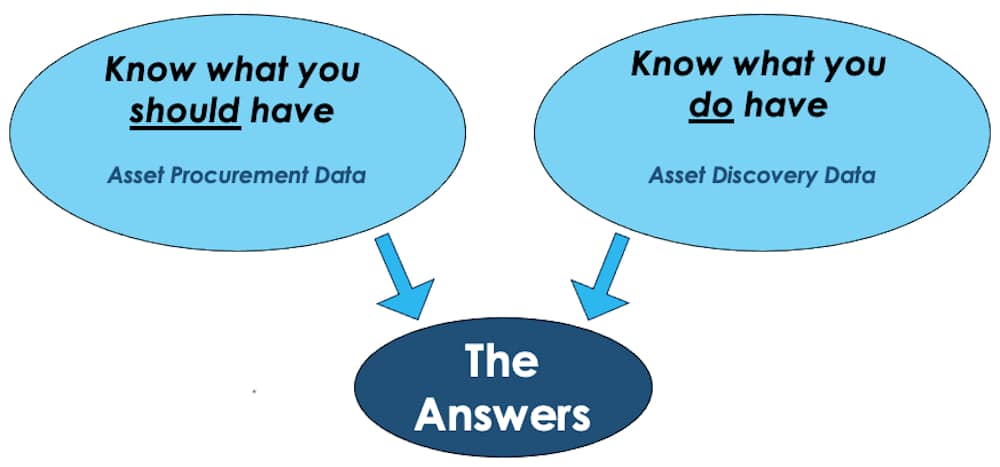
Why Accurate and Timely Procurement Data is Critical and so Challenging to Capture
Accurate and timely purchase data is critical to ITAM success. Without purchase data, you can only manage what you can find
-
Cyber Resilience, Moving Beyond the Buzzword
The term “resilience” is everywhere, but what does it mean to you and your organization. During this presentation, we will define what Cyber Resilience means and how it differs from Business Continuity/Disaster Recovery. We will also discuss some of the findings of the 2023 Absolute Resilience Index Report, to identify some of the challenges you…
-
Create Your Playbook While Maximizing Your Benefits With IAITAM
What do successful sports teams all have in common? A playbook. A list of (offense and defense) plays that each individual member of the team can learn, understand and execute to win. This session will show you how to make the most of your time with IAITAM to move your career forward!





